2.2.5.2. AWS MarketPlace Cloudformation Specifications¶
- creation-day:
Aug. 1, 2022
- update date:
February 2, 2025
The Cloudformation Template (CFT) consists of multiple files, where the parent Stack calls each of its child Stacks. The child Stacks to be invoked depend on the parameters of the parent Stack.
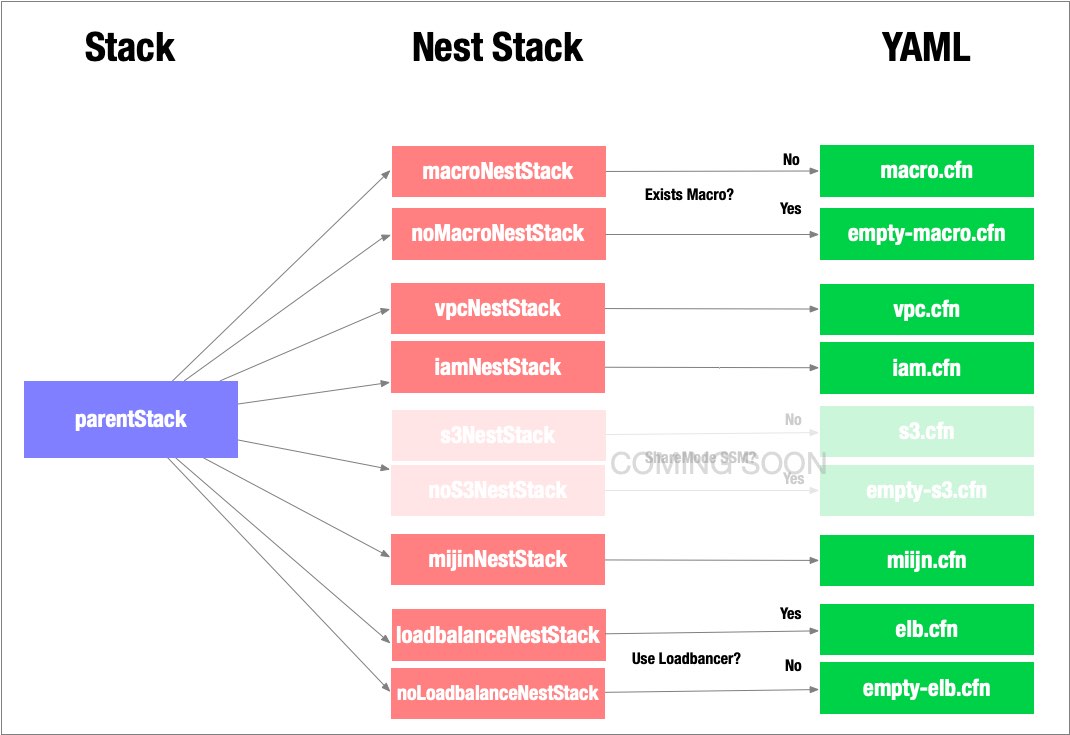
2.2.5.2.1. macroNestStack¶
macroNestStack creates a Cloudformation Macro. If the parameter mijinStackAlreadyExist is Yes, a stack that does not create a Macro will call (empty-macro). This is because the Cloudformation Macro is created with a unique name, so it is not possible to create multiple Macro’s with the same name.
Resources:
PeerUnitsExecutionRole:
Type: 'AWS::IAM::Role'
Properties:
AssumeRolePolicyDocument:
Version: 2012-10-17
Statement:
- Effect: Allow
Principal:
Service:
- lambda.amazonaws.com
Action:
- 'sts:AssumeRole'
Path: /
Policies:
- PolicyName: root
PolicyDocument:
Version: 2012-10-17
Statement:
- Effect: Allow
Action:
- 'logs:CreateLogGroup'
- 'logs:CreateLogStream'
- 'logs:PutLogEvents'
Resource:
- Fn::Join:
- ':'
-
- 'arn:aws:logs'
- Ref: 'AWS::Region'
- Ref: 'AWS::AccountId'
- 'log-group:/aws/lambda/*:*:*'
The Cloudformation Macro is created in Lambda (Node.js) and converts the CFT of the mijinNestStack that follows by the specified parameters.The Macro can replicate the stack of EC2 instances and dynamically change the EC2 instances to be launched, depending on the number of the parameter PeerNumberOfUnits.
Warning
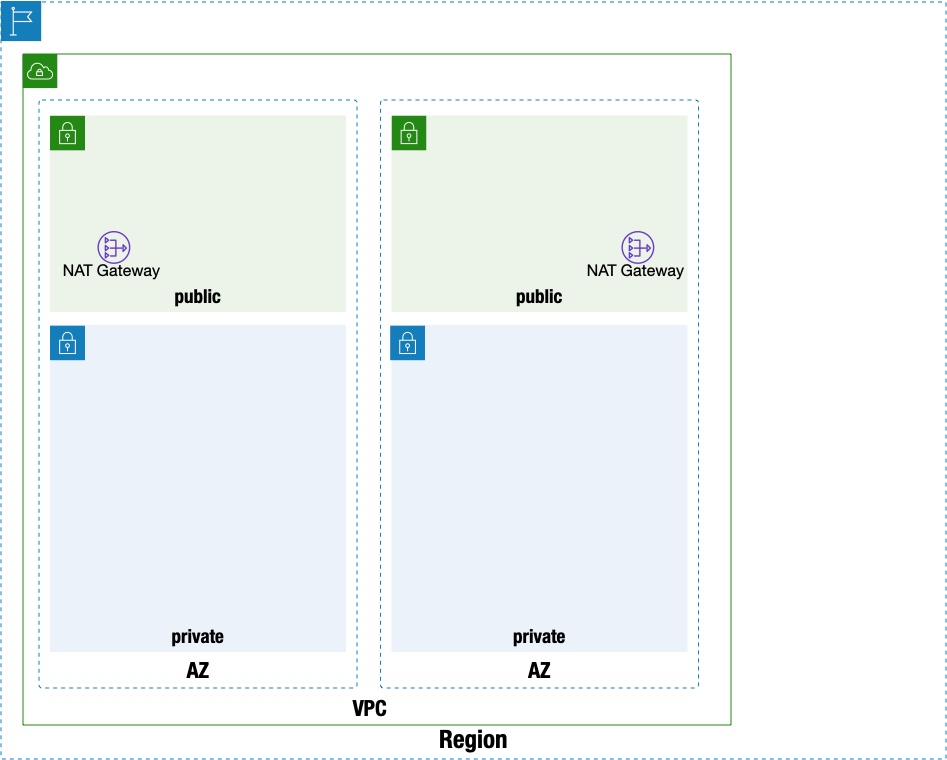
2.2.5.2.2. vpcNestStack¶
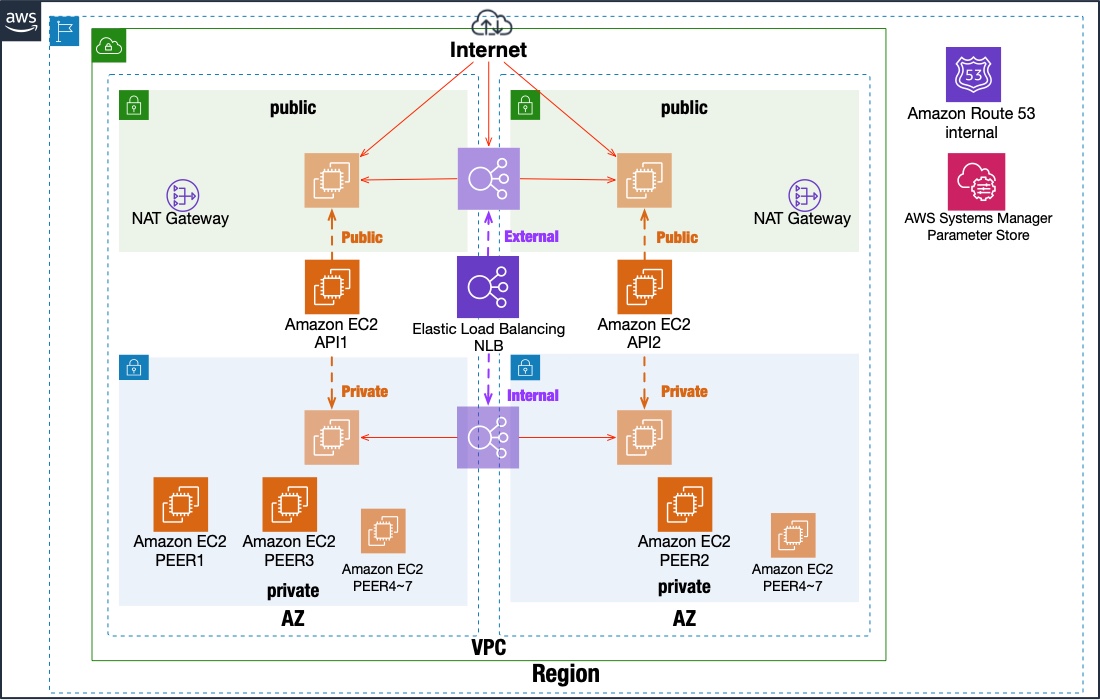
vpcNestStack creates a new VPC. A multi-AZ environment is created, with public and private subnets placed in each AZ. The default gateway for private network routing can also go out to the Internet using the Nat Gateway placed on the public network in the same AZ.
Note
This stack is not used when deploying mijin in an existing network.
2.2.5.2.3. iamNestStack¶
The following are roles to be assigned to each API node and PEER node.
AWSApiAccessRole:
Type: 'AWS::IAM::Role'
Properties:
AssumeRolePolicyDocument:
Version: 2012-10-17
Statement:
- Effect: Allow
Principal:
Service:
- ec2.amazonaws.com
Action:
- 'sts:AssumeRole'
Path: /
AWSPeerAccessRole:
Type: 'AWS::IAM::Role'
Properties:
AssumeRolePolicyDocument:
Version: 2012-10-17
Statement:
- Effect: Allow
Principal:
Service:
- ec2.amazonaws.com
Action:
- 'sts:AssumeRole'
Path: /
AWSSSMRolePolicies:
Type: 'AWS::IAM::Policy'
Properties:
PolicyName: AWSSSMAccessPolicy
PolicyDocument:
Version: 2012-10-17
Statement:
- Effect: Allow
Action:
- 'ssm:DescribeAssociation'
- 'ssm:GetDeployablePatchSnapshotForInstance'
- 'ssm:GetDocument'
- 'ssm:GetManifest'
- 'ssm:GetParameters'
- 'ssm:ListAssociations'
- 'ssm:ListInstanceAssociations'
- 'ssm:PutInventory'
- 'ssm:PutComplianceItems'
- 'ssm:PutConfigurePackageResult'
- 'ssm:UpdateAssociationStatus'
- 'ssm:UpdateInstanceAssociationStatus'
- 'ssm:UpdateInstanceInformation'
Resource: '*'
- Effect: Allow
Action:
- 'ssmmessages:CreateControlChannel'
- 'ssmmessages:CreateDataChannel'
- 'ssmmessages:OpenControlChannel'
- 'ssmmessages:OpenDataChannel'
Resource: '*'
AWSPSAccessRolePolicies:
Type: 'AWS::IAM::Policy'
Properties:
PolicyName: AWSPSAccessRole
PolicyDocument:
Version: 2012-10-17
Statement:
- Effect: Allow
Action:
- 'ssm:PutParameter'
- 'ssm:GetParameter'
- 'ssm:GetParametersByPath'
AWSAssumeAccessRolePolicies:
Type: 'AWS::IAM::Policy'
Properties:
PolicyName: AWSAssumeAccessRole
PolicyDocument:
Version: 2012-10-17
Statement:
- Effect: Allow
Action:
- 'sts:AssumeRole'
Resource:
- Fn::Join:
- ':'
-
- 'arn:aws:iam:'
- Ref: 'AWS::AccountId'
- !Sub "role/${ServiceName}*"
Roles:
- !Ref AWSApiAccessRole
- !Ref AWSPeerAccessRole
2.2.5.2.4. s3NestStack¶
Warning
This feature is currently disabled and only the parameter store can be saved.
s3NestStack allows you to choose whether to place mijin data in the AWS Systems Manager parameter store or in an S3 bucket, and if you choose S3, it creates an S3 bucket.
2.2.5.2.5. mijinNestStack¶
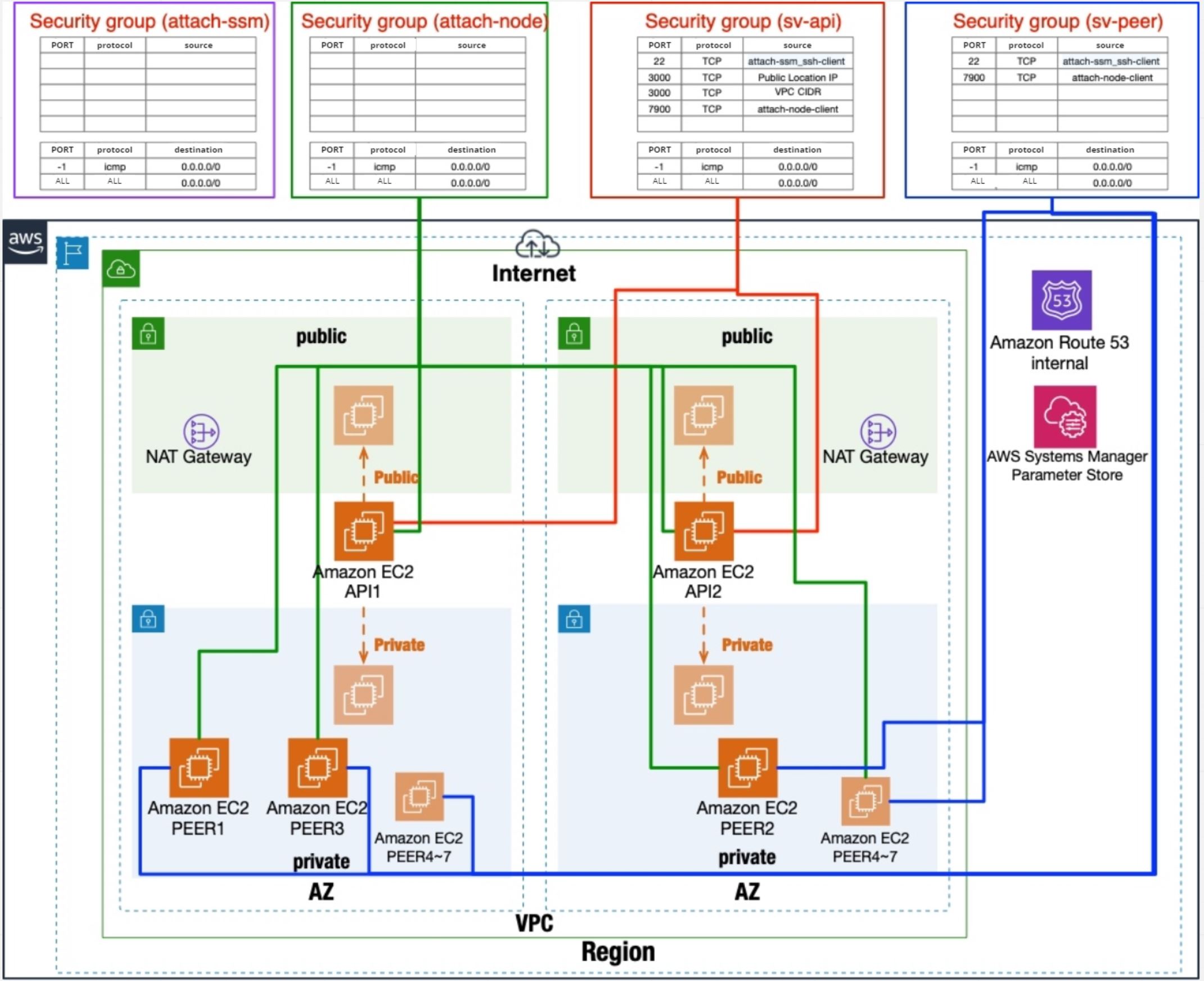
mijinNestStack creates private DNS, security groups, EBS, and EC2 instances with Route53.
mijin uses DNS names to communicate between each EC2 instance. The domain is fixed at mijin.internal, and each instance name is set to the A record as follows.
api1.mijin.internal
api2.mijin.internal
peer1.mijin.internal
peer2.mijin.internal
peer3.mijin.internal
peer4.mijin.internal
peer5.mijin.internal
peer6.mijin.internal
peer7.mijin.internal
peer8.mijin.internal
peer9.mijin.internal
Security groups are applied below, with the minimum security group used for communication as shown in the image.
Security group name |
Description |
attach-ssm_ssh-client |
This security group can be set up as a stepping stone, etc. to allow SSH login. It is not used for new VPCs. (If created for an existing VPC, assign it to an existing stepping stone, etc.) |
attach-node-client |
For inter-node communication. |
sv-api |
This is for API nodes.
3000 port / for REST access.
7900 / For mijin node communication.
|
sv-peer |
For PEER node.
7900 port / for mijin node communication.
|
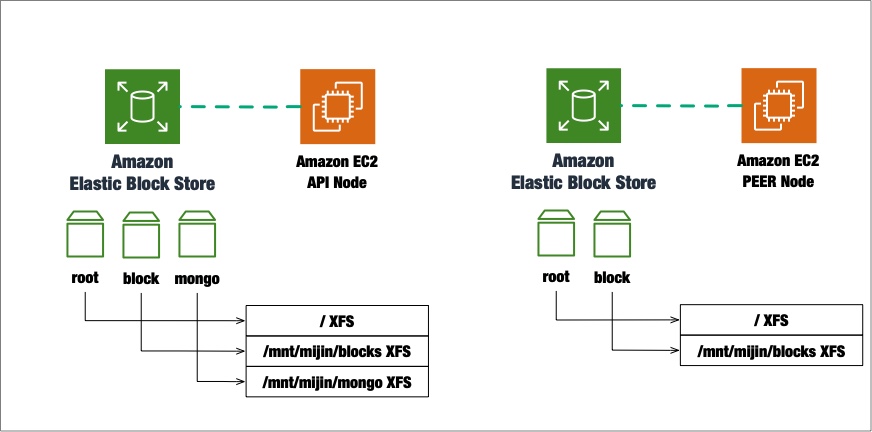
The EC2 instance is started using a custom AMI with the mijin package installed. UserData runs cloud-init and executes the initial package configuration. It receives the results of the UserData execution and rolls back if the configuration fails.
Unix user settings specified by parameter
Host Name Settings
OS package updates
Installing pip
Installing cloudformation helper script
- Setup of mijin
EBS Format
mijin setup (api1 uploads data to parameter store)
ApiInstance1
ApiInstance2 PeerInstanceX Concurrency
Parameter name |
Description |
|---|---|
/Crown name specified at deploy time/shares/api_node.json |
Public key used by the API node |
/Crown name specified at deploy time/shares/generation_hash.json |
mijin Catapult(v.2) blockchain’s Genesis Hash (GenerationHash) |
/Crown name specified at deploy time/shares/harvest_fee_sink_public_key.json |
Address to receive Harvest (not required for mijin) |
/Crown name specified at deploy time/shares/init_host_count.json |
Number of nodes created during deployment |
/Crown name specified at deploy time/shares/mosaic_rental_fee_sink_public_key.json |
Address to receive Mosaic rental fees |
/Crown name specified at deploy time/shares/namespace_rental_fee_sink_public_key.json |
Address to receive Namespace rental fees |
/Crown name specified at deploy time/shares/nemesis_addresses.json |
Empty address not used in particular (can be used) |
/Crown name specified at deploy time/shares/nemesis_addresses_harvesting.json |
Address to receive harvest, etc. |
/Crown name specified at deploy time/shares/nemesis_addresses_harvesting_voting.json |
Address used for authorization to finalize |
/Crown name specified at deploy time/shares/nemesis_addresses_harvesting_vrf.json |
Addresses for enhanced security (to obscure the state in which blocks can be generated) |
/Crown name specified at deploy time/shares/peer_node.json |
Public key used by the PEER node |
/Crown name specified at deploy time/shares/rest_gateway_private_key.json |
Address for REST used by API node |
/Crown name specified at deploy time/shares/signer_private_key.json |
Address to sign Nemesis (Genesis) block |
/Crown name specified at deploy time/shares/new-cert/each node/CA/[*].pem |
SSL certificate to encrypt communications between nodes |
Note
2.2.5.2.6. loadbalanceNestStack¶
Note
TargetGroupAttributes:
- Key: stickiness.enabled
Value: 'true'
NLBs can be parameterized for inward placement for private use only or outward placement for connection via the Internet.
Properties:
HealthCheckIntervalSeconds: 10 # 10秒間隔でチェックする Check at 10-second intervals.
UnhealthyThresholdCount: 3 # 異常とみなす回数 Number of times considered abnormal
HealthyThresholdCount: 3 # 正常とみなす回数 Number of times considered normal
HealthCheckPath: /chain/info # ヘルスチェックをするURL URL for health check
HealthCheckProtocol: HTTP
Port: 3000 # ヘルスチェックポート health check port
